![]() I
Want to Buy a Home I
Want to Sell my House I
am Relocating
I
Want to Buy a Home I
Want to Sell my House I
am Relocating ![]()
Pre-Approve
Me for A Home Loan Update
Me Weekly
With Info
|
|
Anti-Virus Help
Complements of Lori &
"G-II"
Search our List of Viruses
and Virus Hoaxes
Happy99 Pretty Park
Wobbler KaKWorm
Melissa ResumeWorm
Life_Stage
Funny
Joke
FunnyText
LoveLetter NetLogWorm
Network
|
This little guy is a real pest; a lot like
Pretty Park. Learn how to kill it. |
| back to top |
|
Learn how to rid your computer of this pesky
virus/worm |
| back to top |
|
This hoax has been passed on for years.
Learn more about it |
| back to top |
|
This little guy is a real pest but completely
fixable. VBS.KakWorm spreads using Microsoft Outlook Express. It attaches itself to all outgoing messages via the Signature feature of Outlook Express and Internet Explorer newsgroup reader. |
| back to top |
|
W97M.Melissa.BG is a Word 97 macro virus that has a payload of deleting necessary system files. It also sends itself out through e-mail using Microsoft outlook. The subject of the e-mail is "Resume - Janet Simons". |
| back to top |
He's Back!... This little nasty guy is nothing to be messed with... NAV currently detects this worm as Bloodhound.VBS.Worm. This worm appears as an attachment titled LIFE_STAGES.TXT.SHS. Execution of this attachment will open a text file in Notepad displaying the male and female stages of life. Whilst the user is reading the text file the script is executing in the background. This worm spreads itself using Outlook, mIRC and PIRCH. SARC suggests that corporate customers configure their email filtering systems to filter out or stop all incoming emails that have attachments with .SHS extensions. Click here to view NetScape Messanger Rules Window properly configured to delete this incoming virus. Click here to view OutLook Express Rules Filter properly configured to delete this virus from the mail server Click here to view OutLook 2000 Rules Filter properly configured to delete this incoming virus VBS.Stages.A |
| back to top |
| This worm appears to originate from Manila, Phillipines. It has wide-spread distribution, infecting millions of computers. This worm sends itself to email addresses in the Microsoft Outlook address book and also spreads itself into Internet chatrooms via mIRC. This worm overwrites files on local and remote drives, including files with the extensions .vbs, .vbe, .js, .jse, .css, .wsh, .sct, .hta, .jpg, .jpeg, .wav, .txt, .gif, .doc, .htm, .html, .xls, .ini, .bat, .com, .mp3, and .mp2. VBS.LoveLetter.A |
| back to top |
|
This VBS worm does little but replicate. It attempts to copy itself across a network by first locating shared network drives, |
| back to top |
OutLook
2000 e-Mail Rule Filter set to delte VBS.Stages.A Virus from your incoming
mail client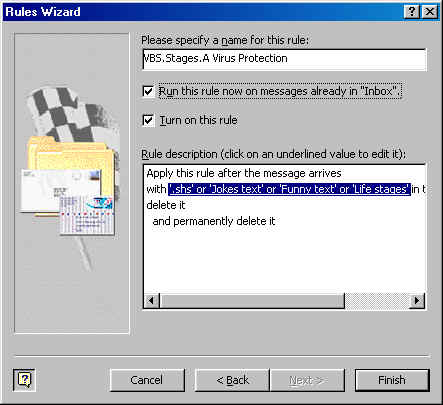 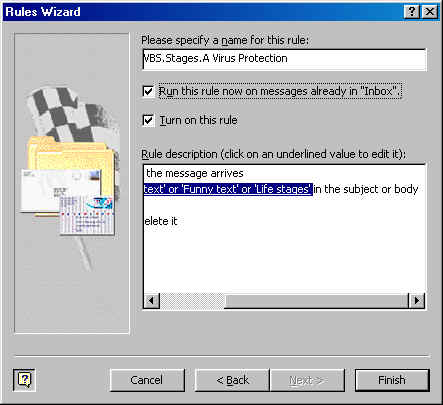 back to top |
OutLook
Express e-Mail Rule Filter set to delete VBS.Stages.A Virus on Mail Server
before it is transmitted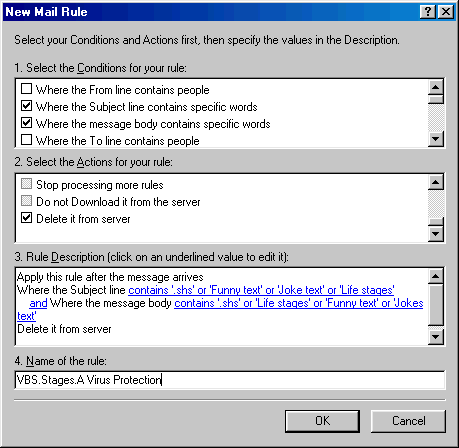 back to top |
Net
Scape e-Mail Filter set to delete incoming VBS.Stages.A Virus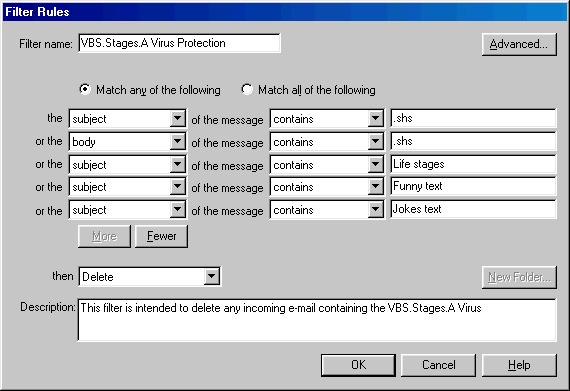 back to top |